eXtra Notes

|
|
 |
Graham K. Rogers |
|
|
|
Previous note (1) can be found here.
Previous note (2) can be found here. Previous note (3) can be found here. Previous note (4) can be found here. Previous note (5) can be found here. |
Previous note (6) can be found here.
Previous note (7) can be found here. Previous note (8) can be found here. |

A slight difference for this xnote as I am going to cover a meeting I attended last night (24 Nov 2004) of the paradise Mac Users' Group, down in Phuket. I was a guest of Sam-Erik Ruttman, manager of the Dusit Laguna Hotel.  The meeting was actually held at The Phuket Boat Lagoon Resort Hotel who had laid on a projector and screen, and was helped by a fair turnout as well as the assistance of Ekawat Chansamutwathana and his team from Phuket's Alpha Engineering, who brought along a dual 1.8GHz G5 for me to play with. As I had also carried down the Wacom Intuos 3 graphics tablet along with my Nikon D70, we were able to cover a wide range of subjects during the evening: details, as best I can remember them follow.
The meeting was actually held at The Phuket Boat Lagoon Resort Hotel who had laid on a projector and screen, and was helped by a fair turnout as well as the assistance of Ekawat Chansamutwathana and his team from Phuket's Alpha Engineering, who brought along a dual 1.8GHz G5 for me to play with. As I had also carried down the Wacom Intuos 3 graphics tablet along with my Nikon D70, we were able to cover a wide range of subjects during the evening: details, as best I can remember them follow.
After a brief introduction by Sam, I thanked him, Ekawat and also John Williams (of Siam Dive 'n Sail) who has been a long-time correspondent: we have solved many problems online.
iPhoto
I decided to start with the camera and plugged in the USB connector causing iPhoto to start up. As it was the first time -- a new machine -- I had to go through a couple of screens and was then ready to import. With iPhoto the camera is automatically recognised, and there are no driver problems. It is a lousy editor of pictures, but I think it is a useful organiser. Importing took a couple of minutes as there were plenty of images and they were large. Using "export" I showed how one image (or several) could be retrieved and used. I showed all of the images using the "edit" function and several of the members expressed surprise at the size we were able to enlarge the pictures on the screen. This was not a feature of iPhoto but was due to the quality that the Nikon produces. I used another function of "export" and showed how to create a "quick and dirty" web-page of thumbnails and images. The images themselves were in the region of 200Kb and so considerably smaller than the 2.8MB originals. We also viewed the source file in Safari and saw how the simple html page produced could be easily edited to improve things.
During the 24 hours that I was in the Pearl of the Andaman, I took a number of photographs. I made a web page using the same method I outlined at the meeting: all the pictures used here are undoctored.
I also pointed out that the "book" function of iPhoto ought not to be forgotten. Although Apple has not brought the book-making function to Thailand, in much the same way as we are unable to buy from the iTunes shop, it is still possible to create a book and print it out on quality paper ourselves, or save it as a pdf.
iPod
Putting in the iPod will usually start up iTunes and, if this is not your usual computer, resist the temptation to press the "return" key when a dialogue box appears. You are being offered the chance to make this computer your iPod computer. In the case of Alpha's G5, with nothing in iTunes, I would have removed all the music in my iPod. Of course, I would have been able to synchronise pnce back in Bangkok, but it was easier to just say, No. Once in iTines, selecting the iPod icon, gives you access to its preferences and it is here that you can turn on "disk use". With it operating as a hard disk, not only can it be used to transfer and store files, but it can be made bootable. I have done this and put on rescue software, including Disk Warrior, but I do not suggest that it is used as a regular hard disk" emergency only for me.
With the iPod plugged into the Firewire port, I put in the Panther startup disks: this will not work with the computers original install disks. Restart using the "C" key and when the installer comes up, select the iPod as the target. It is of useful if the installation is customized and most applications are removed, languages deselected and no extras are put in. I put on only the BSD subsystem and Stuffit Expander. That brings it down to a little over 1GB.
Wacom Intuos 3
As the computer arrived early, I was able to take 5 minutes - which is all it takes -- to install the software for the Intuos graphics tablet. Although I would not profess to any expertise with this technology, it is obviously easier to draw with this than with a mouse. I was able to demonstrate the adding of an application to the Wacom preferences. This allows each application used to have its own settings, if a user so desires.
Random Access Memory (RAM)
While we were discussing aspects of the operations, I interrupted a question about RAM and said, that, in my opinion, you can never have enough. The question really being asked was on how SX differes in its handling of memory allocation. With earlier systems, each program had its own allocation (which could be altered by use of "Get Information") and when an application was shut down, in theory, the memory would be returned to the system. OSX allocates and reallocates as necessary. To demonstrate this, I opened the Applications folder and selected All, then pressed "Open". One by one the folders then the applcations opened. As there were quite a few on the hard disk, this took quite a while, especially as some were being opened for the first time and might require registration or other information.
Security
As this is something I am concerned about right now, I looked at a number of ways that security can affect users:
This week, I had an almost identical message that told me it was from "Sun Trust Banks". I had never heard of this group, so thought it was highly unlikely they would be contacting me. Like the earlier Citibank scam message, this made the threat "This process is mandatory, and if not completed within the nearest time your account or credit card may be subject to temporary suspension". Apart from grammar weaknesses, the lack of a defined time limit makes this highly questionable anyway. In the centre of the message is a link to a web site. Although the Sun Trust Bank does have a website, that particular URL does not exist but if you were to click on it, you would not link to Sun Trust anyway.
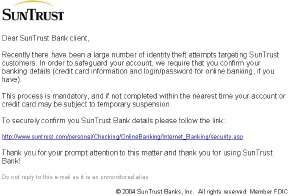
The entire message is a GIF. Click on it and you can drag it to the desktop. Beneath it is some useful information that you can look at in Mail using View>Message>Raw Source. What you see is that the message is a mapped image, with some randown text underneath. The nasty bit is in the middle where the coordinates of the URL send you to another which is coded in hexadecimal. I have removed the last part of the information after the colon:
 Terminal will open looking like a white rectangle with some black letters. You can change the colours if you want (I have in this image -- this reminds me of the original monochrome monitors that were almost universal when I first used computers).
Terminal will open looking like a white rectangle with some black letters. You can change the colours if you want (I have in this image -- this reminds me of the original monochrome monitors that were almost universal when I first used computers).
Terminal is the OSX way to use a command line. It sounds odd for the Mac which pioneered the graphical interface, but (believe me) getting used to this has made my life a lot easier. The commands you need to run are really only for the Root user. Root is the owner of the system. Most of the time we do not use Root as it is dangerous. One wrong keystroke and you could lose everything. Being Unix, there is a way round. If we have an administration account we can pretend to be a substitute user by using the sudo command (this allows Root tasks for 5 minutes) and then entering the neceesary text:
Hit the Return key. The Terminal will first give a warning, and then it will ask for a password. Enter your password and again press the Return key. Let OSX do its stuff and then you will be back to the prompt.
As well as the daily command, there are weekly and monthly commands too. Either type in the command in full or press the UP key and then edit the last command, so you end up with
Have faith with this one. It takes a long time: perhaps as long as ten minutes, depending on the size of the hard disk and the speed of the machine. I also regard this one as the most essential of the three cleanup routines as there are noticeable performance increases on a Saturday morning (it normaly runs during the previous night).
Similarly, the monthly command is
This cleans up the data about the month's logins (useful if you have a few accounts on the machine).
Along with these maintenance tasks, I think that using Disk Utility to repair permissions is also valuable. I run this at least once a week (with MAcaroni it is done automatically), plus before and after installing software. When repair Permissions is run, it always shows the line "We are using . . . . 33261" which is all quite normal. It may or may not show that specific permissions are being repaired, but at the end, you will see "The privileges have been verified or repaired on the selected volume". This can either be run on the disk or the partition. It is useful to check the disk occasionally particularly for the S.M.A.R.T. status which should show "Verified". If that changes to red and has something other than "verified" back up your data (you should be doing this anyway) and save up for a new disk.
Startup keys. I restarted the G5 in single user mode (Command + S) to bring up the raw Unix and show he members what happens underneath the startup procedure. At the Root level prompt, it is possible to run a similar disk check to that run by Disk Utility. The command is fsck -y, for file system check, and "yes" to any necessary fixes. With Panther, however, the default is to have journalling on -- a method of recording what the system settings are -- and the check has to be forced, with fsck -fy or fsck -yf or even fsck -y -f.
We also discussed other start up keys and I demonstrated the "Safe" startup (temporarily disables login items and non-essential kernel extension files) that is effected when the Shift key is held down. There are also the "Command + V" keys for the verbose startup (text appears like the single-user start and it may be possible to see something in the procedure that is causing, for example, a delay); the T key for startup in target mode (one computer connected to another via Firewire). Pressing X during startup forces Mac OS X to startup; Option-Command-Shift-Delete during startup will bypass primary startup volume and seek a different startup volume (such as a CD or external disk); press C during startup will start up from a CD that has a system folder; N will attempt to start up from a compatible network server (NetBoot); R will force a PowerBook screen reset.
Software
As we had talked about some programs like MacJanitor (all of those I mentioned are available from Versiontracker), I realised that I had them with me on the iPod. One of the members came up with a thumb drive and I copied several of the shareware and freeware applications I had with me. There was not enough room to copy the 10.3.6 Combo update that I also had. While going through the list of software, we discussed the value of some and why some were perhaps not so useful.
Endnote
After the photogaphs at the end of the session, one of the members asked me about OSX on a Wallstreet. As luck would have it, a user from the US had also asked me questions about the same computer, so I was armed. The Phuket Wallstreet user had put in a 30G hard disk but had been unale to install OSX. What he needed to do was to partition the disk and install OSX on the first 8G (or perhaps 7.75 as it needs to be less than 8) partition; and the Wallstreet will only run up to 10.2.8 so Panther is out.
I had a pleasant 24 hours and look forward to similar such events which bring other Mac users together. Let us hope that, with sales beginning to rise again, there will be more new users next time round.
All materials ©copyright G.K. Rogers. Free for individual use.
Other links:

|

|

|

|

|

|

|

|

|

|
|

|

|

|

|

|

|

|
For further information, e-mail to Graham K. Rogers.
To eXtensions, Current items
To eXtensions, Year Two
To eXtensions, Book Reviews
To Education Page