eXtra Notes

|
|
 |
Graham K. Rogers |
|
|
Previous note (1) can be found here.
Previous note (2) can be found here.
Previous note (3) can be found here.
Previous note (4) can be found here.
Previous note (5) can be found here.
Revised 1 November 2004
 It was packed, with all the Linux machines taken over by crowds of people, of all ages, with a few black suits still milling around and some photographers getting copy. In the middle of the room is a round glasshouse with the G5 iMacs in a circle. I still have not counted them but it looks to be about twenty.
It was packed, with all the Linux machines taken over by crowds of people, of all ages, with a few black suits still milling around and some photographers getting copy. In the middle of the room is a round glasshouse with the G5 iMacs in a circle. I still have not counted them but it looks to be about twenty.
I walked in, sat own and started to look. A few people were there, but nothing like the density of the PC-shaped machines outside. I was not wholly impressed with these G5s initially as there had obviously been little (or nothing) done to set them up properly. I adjusted the size of the Dock and checked "About this computer." With only the standard 256MB of RAM, these are going to be gasping if the intention of the ICT Ministry is to allow out-of-work graphics experts loose on these.
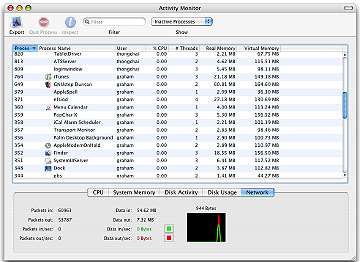
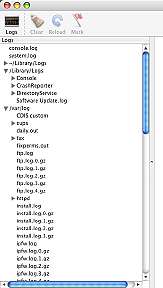
I looked deeper starting with Activity Monitor to see what was running. The machines are switched off every day and this is shown in the Console logs, as well as everything that occurs on the machine.
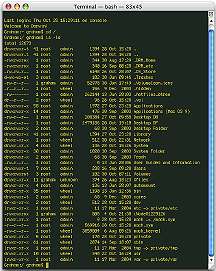
I had a look at Terminal and tried to run the scheduled daily maintenance. That is the one that runs if you leave your OSX Mac on 24 hours a day. And if you do not, it is a good idea to run these from the command line. The housekeeping that will be done when they run, keeps the machine in better order. I have written about this many times in columns, and have some information on a suggestions page I maintain. Apple do not seem to make this information widely available (they do have it but you have to dig) and that means many users clog up their computers: Not only is OSX not Windows, but it is not OS9 either.
|
|
As I was in Terminal, I ran a few commands to look at the structure and to get a feel of the installation. All the while, no one is looking over my shoulder; nor is anyone checking what is being done to the entire installation. One of the commands that I ran was "last" and that command proved that the maintenance had not been run as the whole login history since 30 September was there. Only Admin was shown.
I opened System preferences for a couple of reasons. Firstly to look at the network: none, although this is touted as a service to allow people to access Internet resources easily. Maybe it was just off for that day: Saturday. And then I looked at the Accounts preference.
I owned the computer.
Or at least, with the "lock" undone. The only user was Admin, and the password box was wide open for anyone to change, I could have locked out the ICT Ministry staff and done mucho damage.
Fortunately, I have ethics as far as other people's computers are concerned, especially a setup like this where the computers are made available for people to learn on. I had a quick look round and saw the office, so walked over and found the Director of NICT, Dr. Virach Sornlertlamvanich. To his credit, I interrrupted what he was doing, but he came over and listened to my brief outline of the situation as I saw it. He tried to contact the "Mac Man" but could not get through and said he would get him to call me. We exchanged cards.
While we were discussing the openness of these machines, he admitted that, a few days into the program, the other machines were riddled with viruses. I mentioned that there was now one on the OSX platform (called "renepo"), but added that this is only an experiment and has no delivery system.
This sort of brings me back to where I had intended to be (and was this morning). A lot of words have been generated in the last seven days about this so-called OSX virus and what has both amazed me and peeved me is the way some of the press have gasped and shouted it from the rooftops. ONE virus. How many do Windows users have to combat each year?
Despite what Gates and Ballmer would want you to believe, the lack of viruses on the Mac platform is not down to its small installation base. There are solid technical reasons, partly because of the Unix, and partly also because of the way that (unlike Linux/Unix) it is not easy to access root. Indeed, there is little need for root to be activated; and any installation of applications, such as that renepo virus ("opener" backwards), can only be done if you enter the Administrator's account name and password. As one Apple forum writer put it, with the amount of effort needed to install this malware, it would be easier to "steal the machine off my desk."
Bearing this in mind, I was mildly amused by the front page Database letter this week from Miles Ignotus. I read this carefully and was almost open-mouthed at a couple of points: the things he claimed he had to do to keep a clean system. I knew that Windows users had it hard, but this letter was a clear indication to me about just how dedicated (or masochistic) Windows people have to be. One thing they need to remember is not only that the firewall is turned off by default but that the computer also sends lots of little data points to the Beast of Redmond as well.
With that in mind, although my firewall is on, I decided to download a utility that has long been talked about on forums, Little Snitch. To quote some of the rubric on the website:
 Little Snitch has a demo mode of 3 hours and then a licence costs $24.95. With an ADSL connection, there may be more time for miscreants to try to access one's online computer; or for software writers to include routines that send data "home". Some of these are legitimate, for example when a program reminds me that there is a new version: with Little Snitch I can now choose to alllow or refuse that connection. As an example, I tried to FTP to my eXtensions pages but Little Snitch came up instantly to warn me of the attempt. It also recognised the application I use as a program and gave me the option to allow this access, Now, Forever or Never (Deny), and also gave several options as to the server used at the other end. When the 3 hours is up, you can restart the applicaton using the icon in System preferences, but this is likely to end up as another online purchase for me.
Little Snitch has a demo mode of 3 hours and then a licence costs $24.95. With an ADSL connection, there may be more time for miscreants to try to access one's online computer; or for software writers to include routines that send data "home". Some of these are legitimate, for example when a program reminds me that there is a new version: with Little Snitch I can now choose to alllow or refuse that connection. As an example, I tried to FTP to my eXtensions pages but Little Snitch came up instantly to warn me of the attempt. It also recognised the application I use as a program and gave me the option to allow this access, Now, Forever or Never (Deny), and also gave several options as to the server used at the other end. When the 3 hours is up, you can restart the applicaton using the icon in System preferences, but this is likely to end up as another online purchase for me.
 Rule of thumb here (see the G5 item above): if I can get into your computer, anyone can.
Rule of thumb here (see the G5 item above): if I can get into your computer, anyone can.
As is the perverse nature of things, as soon as I put a web-page up (or submit an article), new information arrives. This is going in bold red: The United States, National Security Agency has released a pdf file on OSX, 10.3 (Panther): a Security Configuration Guide. This is one of the clearest guides to OSX configuration I have seen for the more aware user (Pogue's Missing Manual series from O'Reilly is great to get you started). There are some processes in the NSA guide that are not covered in Pogue, and with the way that the NSA treats this as a serious subject, it is a valuable download for the technical minds among you. As an aside, the site address is not www.nsa.org but www.nsa.gov and the other has a degree of satire.
I also found that there are several NSA guides (for other operating systems) accessible on the NSA website.
I have been reading (prior to writing reviews) some books on security. I even tried some of the legitimate tricks that these works outlined and it is surprising what you can find out. My venture into the G5 security problem (above) might some under the heading of "social engineering" but I had a good example of that myself this week.
A Mac-using friend asked for help getting her networks setup. She carries a laptop between home and work each day and has different settings. Easy to do in System preferences > Networking by using the "Locations" button at the top of the panel. A different set of parameters for home and away; and all you do is select the location you are in and click "Apply" (at the bottom right of the panel).
So having cleared that little problem, I wanted her to test it out at the office by visiting a website. Up came the username and password box and she dictated it to me. I know she trusts me, and I know I am not going to do anything wrong (even if she does have a US credit card and can download from the iTunes shop), but handing over passwords is a route to problems.
All is well in the land of ADSL. I mentioned the Billion driver to a colleague who has been a longtime Windows, Unix and Linux systems user -- he teaches security and networks to the students and is another of the widening bunch of those I know who have gone Mac. In his case, he now has one of the 15" PowerBooks but is low on RAM. I saw him a day or so later and he had downloaded the driver from Billion -- not TRUE you note -- and had it set up.
All that non-Mac awareness is unwillingness to deal with potential customers. I think that the modem/router is a more efficient (and elegant) solution, but the USB modem will work for Macs once you find the driver. The reason my network-savvy colleague is sticking with the USB box is the same as his reason for low RAM. With the extremely low salaries the government (all of them here) pays the academics, despite the hours they work and the responsibilties they carry, RAM or a modem/router is a luxury.
Porn anyone?
A more disturbing problem connected to security is the ease with which unsavoury images on certain sites may be seen. This was brought home to me recently when I was looking for information on a pop group (which for reasons that will be obvious below, I decline to name). As I do normally, I entered the name into Google and up came loads of possibilities -- a simple search word can come up with (say) 20,000 or more links. Some were recognisably the group sites, but others were also obviously not.
I clicked on a few of those that were neither and was disturbed to find that some of the images -- one click away from Google remember -- were not what I would ever want my mother to see. Nor, for that matter would any parent want ther offspring to view this sort of thing either.
It is not hard to see why those who demand that there be Internet legislation believe that they are correct. I would not want there to be such laws, for reasons of free speech, although I would want there to be control of online business transactions and (international) protection for consumers. The two are not going to be separated unless we are lucky.
Talking of censorship, if you try to access the website of PULO, the Pattani United Liberation Organisation (changed from PLO to avoid confusion, I guess), you are redirected to the website of the Royal Thai Police. On the other hand, Aljazeera is freely accessible; and it does carry what reads like the same news carried in publications like the Economist and others.
All materials ©copyright G.K. Rogers. Free for individual use.
Other links:

|

|

|

|

|

|

|

|

|

|
|

|

|

|

|

|

|

|
For further information, e-mail to Graham K. Rogers.
To eXtensions, Current items
To eXtensions, Year Two
To eXtensions, Book Reviews
To Education Page