|
|
When this first occurred, with the help of the local police we managed to track down the location, but by the time we arrived (I was asked to go with them to help identification) it had gone and has only resurfaced once in the meantime, but the screen images I was sent did show that the hard disk, with my accounts was still intact and I keep my fingers crossed. It was interesting to see that the latest iteration of the software now uses additional technology to help the law enforcement agencies track down a stolen computer, by way of the location service provided by Skyhook.
This also works with the iPod touch and I added my data to the Skyhook service a year or so ago. What I did was detailed in my podcast number 131 and the text is online still. There were some follow ups in the next couple as well (132, 133). To send the location of the wifi antenna to Skyhook (and it must be your wifi), you need the co-ordinates. In Google Maps, once you have the location centred, put the following script in the browser address bar.
The contact page of Skyhook has a link to a form for submission of location data which includes some useful information. The original article that I took information from by Dan Moren, is still available online.
The IP number is a problem sometimes. From my own experience in Thailand, where the police were less conscious of computer crime when my PowerBook was stolen, it took far too long for the paperwork to be processed and a location produced. The location itself turned out to be a sensitive area that needed cooperation from another branch of the authorities here, so the computer was gone by the time we arrived. Adding location data from Skyhook may be a way that the difficulty in getting information from an IP number as will happen in some countries, may be less of a problem and that this may ease the process.
Undercover can only be removed by an Admin user, but with OS X disks (or the installation disks) it is possible to change the password of any account. To prevent startup with a disk, users need to make sure that the Firmware Password Utility is installed and working: this can only be done from the Admin account. Should a Mac be stolen, an owner notifies Orbicule and sends a code that was produced at the time of installation: this sets the process going and the Orbicule database flags the specific machine as stolen and monitors for location data. After a time, if the Mac is not recovered, there is a plan B in which the computer appears to be faulty. It is hoped that the machine is either sold or is sent to a repair shop. If this is the case, a message appears on the screen indicating it is stolen. Full details of how this operates are on the Orbicule pages and there are a number of recovery stories available there as well, unfortunately not mine, but I live in hope. The cost of the software is $49 although there are student ($39) and family options ($59) available as well as site licences ($249) with a volume licence for educational establishments at $9.99 per Mac when ordering 100 copies or more. Installation is fairly straightforward and does require a restart. Full information is available on the site. When the computer restarts, a panel appears and the licence information is entered at this time. It is also possible at this juncture to go to the online store and purchase a licence. Once done, the application appears to sleep, but is ready should the unfortunate event of a theft ever occur.
|
|


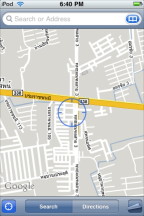 This will reveal the co-ordinates and these can be sent to Skyhook. When I did this it took a few days before an email acknowledging the location data, and a couple more before I could see my location with Google Maps on the iPod touch. That location should be available to anyone and it is this that Undercover is now taking advantage of.
This will reveal the co-ordinates and these can be sent to Skyhook. When I did this it took a few days before an email acknowledging the location data, and a couple more before I could see my location with Google Maps on the iPod touch. That location should be available to anyone and it is this that Undercover is now taking advantage of.