
Thammasala Police Station
eXtensions
|
Undercover with the Thai Police: or how my stolen PowerBook phoned home and we missed the call |

My own complacency with regard to home security lost my PowerBook last month when late one night thieves forced the front door while I was asleep; but security software I had on the Mac almost paid off. When I first wrote about the theft, I did not mention that it was being tracked: I had both the IP number of its location and several screen shots.
 I had installed Orbicule's Undercover, but of course I hoped I would never use it. The opportunity to test it for real came when my house was burgled and several items were taken, including my 12" PowerBook. My emotions in the next weeks ranged from initial disbelief through anger, incredulity, relief and (above all) frustration.
I had installed Orbicule's Undercover, but of course I hoped I would never use it. The opportunity to test it for real came when my house was burgled and several items were taken, including my 12" PowerBook. My emotions in the next weeks ranged from initial disbelief through anger, incredulity, relief and (above all) frustration.
At the same time Orbicule told me the IP adress, Captain Mongkol Puvaphrapachat of Thammasala police also had email and his officers began the discovery process.
Rightly, ISPs in Thailand will not reveal information about an IP address without the correct documentation. Unfortunately, the time taken to reveal the location was too long.
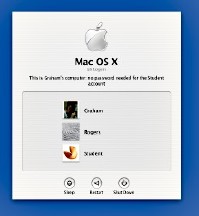
When Undercover was installed, I had followed the suggestions carefully. While there is always an Administrator account with OS X, I always work in a separate User account. Both have password protection. I also created an account with no password: a honey trap.
The thief is drawn to that unprotected account. Using parental controls, I limited some functions of the operating system, and set it up so that some programs could not be used. I installed Open Firmware Password, to lock the system: the computer cannot be started with external disks.
The way I had the Mac locked up may be inconvenient for many people, though what is more inconvenient than a stolen computer? Like insurance, you hope you never need it, but when you do, you are glad you made the effort.
I notified Orbicule of the theft within a few hours and the database was activated. If my PowerBook was used online, it would sent signals and the tracking process would begin. Peter Schols of Orbicule warned me, however, not to get my hopes up early: most connections do not occur for a couple of weeks. That comment was almost a prediction: on day 13, he sent me and the police the IP number.
Subsequently, I saw screenshots that the installation had taken. On the latest Macs with iSight cameras, Undercover also takes pictures of the user, "in the act".
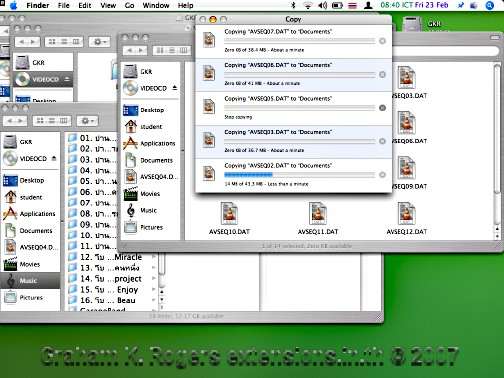
 Although there was no information that identified the user, I was able to build a profile:
Although there was no information that identified the user, I was able to build a profile:
Whoever was using the PowerBook watched "Crank," as well as country style karaoke (I made a note to delete that account), and had imported several megabytes of music and movies. He also contacted the iTunes shop in Japan.
During five days, the computer stayed in the same location with external and internal IP numbers unchanged. This indicated a manual setup, not DHCP, which the Mac has to use in certain situations. He too was probing: trying applications, examining the directories where my folders were still locked. Free space on my hard disk was diminishing.
I was watching a stranger tamper with my carefully maintained computer. Then it stopped.
Information about the location was not available until three weeks had passed. Then there was a burst of activity from the police who, like me, could sense a result and perhaps even the return of the loot.
Sergeant Wanchai Ackrawong visited my home and requested extra information which was able to provide. He also asked me to go along as I could positively identify the computer.
On the following Monday, Wanchai and his enthusiastic team of Prateep Sophee, Teerasak Sudtanin and Veerapong Korseay ferried me to an establishment in the Din Daeng area. Sergeant Wanchai had the foresight to bring his English-speaking son, Joe, as translator.

Initially, Wanchai negotiated with officials to confirm IP details and other information. As it was not possible to conclude the business, we returned the following morning.
Despite cooperation, the computer had probably not been there for several days. Although I was allowed to link to the network and I was able to confirm the settings, there was no trace of my computer. At this stage, I do not expect to see it again.
 That Undercover did manage to track the computer is a positive. I immediately bought another licence for the replacement MacBookPro. That the police cooperated as much as they could was also a plus. We hear negative reports about some officers, particularly in the Metropolis, but those I came into contact with were helpful and keen within the limits of what they were able to do.
That Undercover did manage to track the computer is a positive. I immediately bought another licence for the replacement MacBookPro. That the police cooperated as much as they could was also a plus. We hear negative reports about some officers, particularly in the Metropolis, but those I came into contact with were helpful and keen within the limits of what they were able to do.
A lack of security in the home lost me my computer, but good software (plus cooperation from my local police) almost got it back.
This theft was a minor event when compared with other crime that takes place. It is clear that, while this suburban police station was more used to traditional types of behaviour, computer crime will increase. Officers must be able to deal with this. A three-week wait for an address is unacceptable.
When serious crimes involve computer-use, swift identification of suspects is essential, particularly when considering the mobility that a notebook computer and modern connections permit.
Better liaison between the relevant agencies, including ISPs, with perhaps even the creation of a specialised (but independent) unit for the purpose, would remove such delays, otherwise the authorities' hands are tied.

When a victim of a theft informs the company, by email or phone, using a machine-specific code, provided at the time of initialisation and online registration, a database is activated and the hunt begins.
A computer using Undercover sends out a signal when online. In normal circumstances, nothing happens, but when the database is activated, the fun begins. Details of the IP numbers (internal and external) transmitted by the lost computer are sent to the police officer in the case and to the Internet Service Provider (ISP) so that they can expect contact from the police.
With cooperation, the physical location of the computer is found and the police can then act. As well as the IP details, the software installed will take screen shots while the computer is being used. In some cases (such as email) these can help identify the new user. The latest Macs also have iSight cameras installed and Undercover also takes a picture, so that the miscreant can be positively identified.
The Orbicule website is at http://www.orbicule.com
For further information, e-mail to
Back to
eXtensions
To
eXtensions: 2004-05
To
eXtensions: Year Two
To
eXtensions: Year One
To
eXtensions: Book Reviews
Back to homepage