Security Concerns when Disposing of Hardware

AMITIAE - Monday 13 May 2013
|
Security Concerns when Disposing of Hardware |
 |
|
|
By Graham K. Rogers
Many will use an easy to guess telephone number, a social security number or a variation of the owner's name. If you have bought an Apple computer in Bangkok and asked the store to set it up, the chances are the account name is Apple and the password is simply the Return key (Enter). I always take mine home, format the disk and start again, adding a user account to the required Admin account, and working from that. While the computer is in the hands of its original owner, it is presumably safe. Presuming it is not lost or stolen (when Apple's Find my Mac can delete sensitive data) eventually the computer will reach the end of its useful life at which stage it may be handed on to someone in the family, or sold. Within the immediate family security problems should be limited, but if the computer is to be disposed of outside the home (or business) care should be taken to make sure no sensitive date is left on the device. A quick and easy way with a Mac would be to use System Preferences > Users & Groups to create a new account (or accounts) and then remove the former ones. For some that may suffice, but if the data that was stored on the computer is sensitive (company, personal, financial) users may want to take further steps and reformat the disk. As with the creation and deletion of accounts, however, with a simple one-time erase (or format) data can be recovered. In Disk Utility, the Erase tab has an Security Options button that reveals a slider marked Fastest to Most Secure.
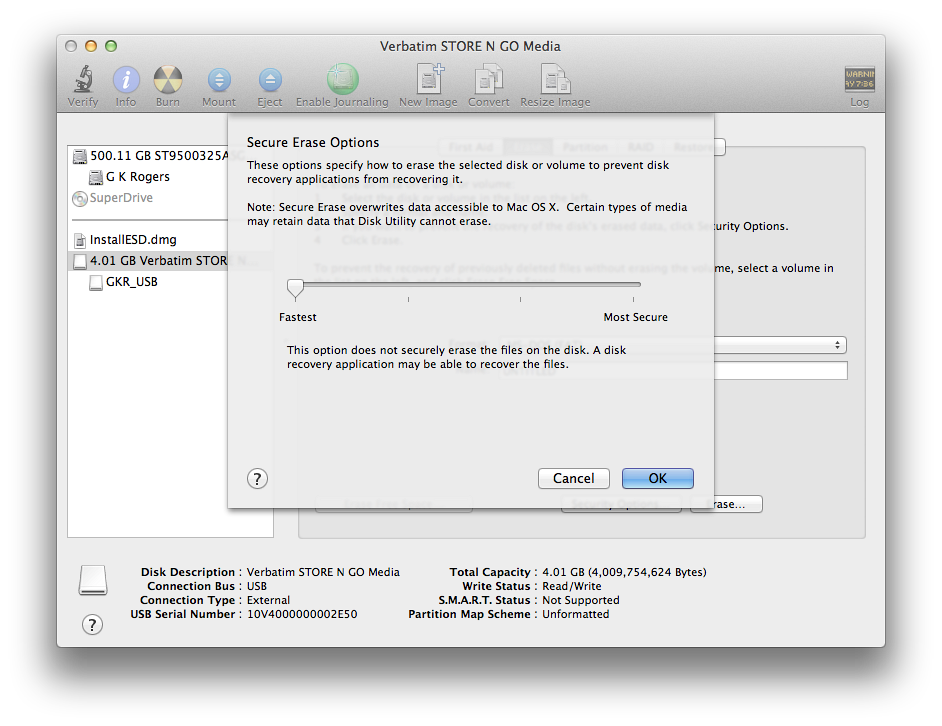
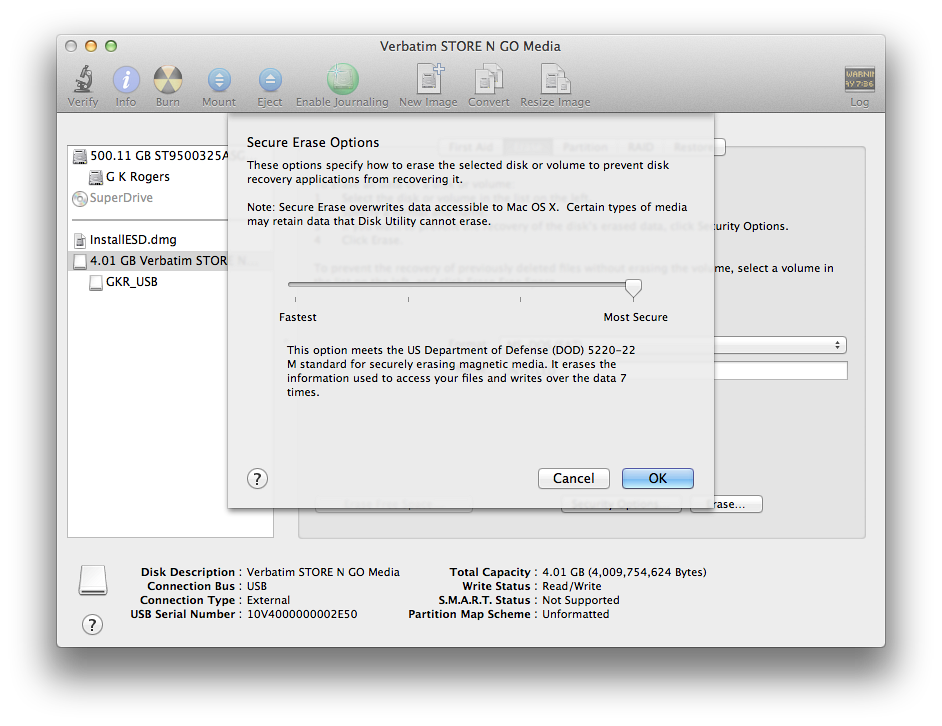
While he is aiming his words at IT professionals, the home user has just as much risk if personal data were to be used by unauthorised persons. Consider carefully how to delete any data before disposing of computers or external media.
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand where he is also Assistant Dean. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. |
|
For further information, e-mail to

|

|