|
 |
eXtensions
|
A Fifth Dimension: Safe Computing Concerns |
Air traffic controllers take several minutes looking at radar screens before announcing "I get the picture" and taking over. When I take a look at someone's computer, I do not just look at directory listings. To have a complete picture I take account of software genres, file types, locations, and (when I can) usage patterns, including passwords, logs and connection types.
I bumped into a friend, Joe, at the beginning of September. He had recently bought a new 1.33GHz, 12" iBook. It was a chance to compare my PowerBook and this tasty white machine back to back.
The first thing he asked was "How do I stop my friends using my computer?" A simple question on the face of it, but in the social environment that exists in a Thai university, this may not be so easy, especially if the students are older "brothers". (Cultural note: seniority is important in Thailand, not the least in student relationships.)
I would tell them: perhaps he cannot.
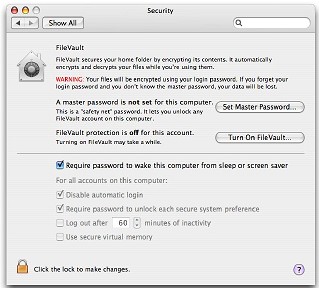
I am concerned if a wayward finger approaches the screen. I suggested the password-activated screensaver. We looked at the Security panel in System Preferences and checked the box that requires the password for screensaver or waking from sleep.

|
 |
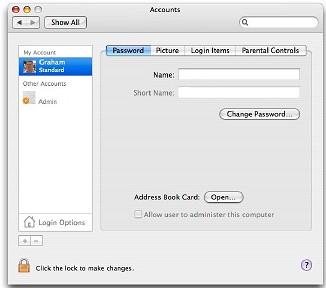
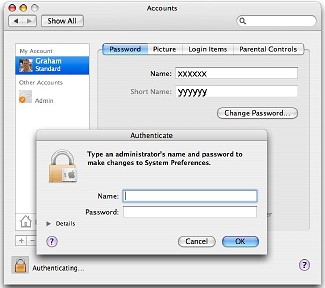
There was a minor panic when the preference reported that there was no password, so Joe made one up and I demonstrated the operation in the Accounts preference.
Not having a password worried me, so I looked further in the Accounts preference and saw how the computer had been set up at the shop. It is policy locally not to use passwords: that is up to the owner. However, the idea behind the password does need to be pointed out. As on Windows machines, too many owners have the Return (Enter) key as the password. That can be devastating in the wrong hands, or even in the owner's.
|
|
Use the Accounts preference and make a new Administrator account, then delete the one that the shop sets up as soon as you are sure it is not needed. I have a "working" account too and rarely use the Admin. one. I enter username and password if needed. As Root does not have a password by default, there is then less risk.
Some people prefer not to have to bother with passwords when logging in. This is possible too in the Security preferences, but running without a proper password is not safe. Joe was the third person I had come across recently with no password protection.
When I looked further, it became apparent why the computer had been configured by the shop, and what the potential for damage could be with no password. Like many other machines sold here, this was loaded with software that Joe was never going to use. Apart from a user's responsibilities, some of the installations might be risky.
An example was a virus application from a company with a less than stellar reputation among OSX users. The software is one of the rarities that puts its tentacles so deeply into the operating system that it takes special software to remove it (a well-known office suite similarly attaches its tentacles into the Root level). Usually OSX applications are uninstalled by simply moving to the Trash. This type of virus application is a waste of space, too, because updating the virus definitions does nothing -- no viruses equals no definitions (except for the Windows ones) -- and yet the applications still goes through the motions on startup.
With those preloaded programs, there is also the space factor. I saw one machine that had 20GB (Gigabytes!) of un-needed software that the new owner had never asked for and would never use. Joe's iBook had a well-known office suite, plus NeoOffice/J (Open Source), as well as the bundled Appleworks. Many of these programs duplicate applications bundled with OSX.
Without the password, and with his friends sticky fingers all over the iBook, I found some other unofficial installations. In the main directory were a couple of .exe files. In case anyone is unsure, these are for DoS and Windows machines and will not run on OSX (which excludes the majority of viruses of course).
There were also about 50 .bmp files installed in the same location, along with an autorun.exe file. The penny dropped. One of Joe's "friends", despite being told it could not work, put a games CDRoM in and copied the files across in the hopes that it would run that way. Ignorance (on the part of his friends) is going to cause easy-going Joe some problems if he does not batten down the hatches.
To help with this, I suggested he also tick the box in Safari preferences that prevents automatic opening of what Apple calls "safe" files. Control what you download and open yourself.
The Mac is not immune to security problems but a little tightening of practices (and settings changes) can minimise problems. Security is not an option.
For further information, e-mail to Graham K. Rogers.
Back to
eXtensions
To
eXtensions: 2004-05
To
eXtensions: Year Two
To
eXtensions: Year One
To
eXtensions: Book Reviews
Back to homepage