
eXtensions - Friday 29 December 2023
By Graham K. Rogers

Apple has appealed the ITC decision on the Watch and for now it can be sold in the USA while a decision or a fix is found. Kaspersky reveals a 4-year backdoor insecurity on iPhones affecting diplomats and others in Russia allowed by a previously-unknown hardware feature. Most connections to computer use WiFi, but the networks still rely on Ethernet or LAN, developed 50 years ago at Xerox PARC.
I thought I would write an end of year comment, although there are no predictions, other than the obvious: new iPhone (sites have been writing about this since the iPhone 15 came out); new Macs, building on the Apple Silicon already announced; iPads (my money is already earmarked for the M3 iPad Pro); plus software developments. That is as far as I go. As many online experts have found, if you make a prediction about Apple, you can be wrong. That applies to Wall Street too, who still do not understand what Apple does, or how. Same day predictions from so-called expert analysts, will have one outlining expansion with another predicting doom. Look at the Stocks app and examine the "all time" chart. A happy new year to all.
 As expected, Apple is to appeal the decision by the ITC. Although the Watch is currently unavailable in the USA, the appeal will allow its sale temporarily. There are also reports that, despite this and the possible licensing (or other financial approaches), Cupertino is still working on a software solution. When I went in to the Apple Store at Central World, Bangkok, this weekend to buy a new watch band, the Watch was certainly on sale: the import and sales ban is US-only of course.
As expected, Apple is to appeal the decision by the ITC. Although the Watch is currently unavailable in the USA, the appeal will allow its sale temporarily. There are also reports that, despite this and the possible licensing (or other financial approaches), Cupertino is still working on a software solution. When I went in to the Apple Store at Central World, Bangkok, this weekend to buy a new watch band, the Watch was certainly on sale: the import and sales ban is US-only of course.
However, Brian Heater (TechCrunch) writes that as the appeal has been filed, the ban has been temporarily lifted and the Watch can be sold (and imported) in the USA. This was reported widely and several other sources carried the information.
Heater's article also gives some useful background to the dispute, concluding that "Masimo has implied that it could be open to licensing the technology to Apple for a fee", although Apple is going to look at all legal avenues first. This is such a valuable feature on the Apple Watch, so maybe Apple should bite the bullet on this one

I follow reports about iPhone security fairly closely and this week was disturbed to read a detailed article (also) by Brian Heaton (ArsTechnica) on an attack that was discovered by analysts at Kaspersky, some 4 years after it had been initiated. They found the backdoor attack on "dozens if not thousands of iPhones, many of which belonged to [their] employees". Further to this, Russian officials report that this had ". . . also infected the iPhones of thousands of people working inside diplomatic missions and embassies in Russia. . . ."
Kaspersky claims that Triangulation - the name they use for this - exploited four critical zero-day vulnerabilities . . . before they were known to Apple. The insecurities have since been patched we are told. However this becomes even more interesting when it was found that the exploit was able to target a previously unknown hardware feature on the iPhone which is "also present in Apple's M1 and M2 CPUs."

The Russian National Coordination Center for Computer Incidents said the attacks were part of a campaign by the NSA to infect iPhones belonging to staff of diplomatic missions and embassies in Russia, "specifically from those representing NATO countries, post-Soviet nations, Israel, and China". The FSB, "Russia's Federal Security Service, alleged Apple cooperated with the NSA in the campaign", which I think would be unethical if true (and proven). Apple declined to reply.
The paper was presented at the 37th Chaos Communication Congress (27-30 December). A research paper was also released this week: Operation Triangulation: The last (hardware) mystery. The writer, Boris Larkin, whose detailed analysis is worth reading, closes the paper with, "Systems that rely on "security through obscurity" can never be truly secure."
 In the history of technology, two establishments stand out: Bell Labs, where some of the major technological developments occurred (including the transistor - which won one of Bell's nine Nobel Prizes); and PARC or Palo Alto Research Center that was set up by Xerox. Bell Labs also developed the laser, the charged-coupled device and photovoltaic cell as well as information theory, the UNIX operating system and the C programming language.
In the history of technology, two establishments stand out: Bell Labs, where some of the major technological developments occurred (including the transistor - which won one of Bell's nine Nobel Prizes); and PARC or Palo Alto Research Center that was set up by Xerox. Bell Labs also developed the laser, the charged-coupled device and photovoltaic cell as well as information theory, the UNIX operating system and the C programming language.
After the court-ordered breakup of AT&T, Bell Labs was bought by Lucent and subsequently Nokia, which enjoys a rich collection of patents. I recommend Jon Gertner's 2012 book, The Idea Factory: Bell Labs and the Great Age of American Innovation for its wealth of information, and surprises. It is published by Penguin, although I bought the eBook from Amazon.
PARC, which still exists, was famous for the graphic user interface and the mouse that Steve Jobs spotted on a visit. PARC was also where Ethernet, which this year sees its 50th anniversary, was developed (Joanna Goodrich, IEEE Spectrum). Many people refer to this nowadays as LAN (or local area network) although I prefer the original term. This and the modem were how we connected to the internet before WiFi existed and it is still widely used.
I link my Apple Airport WiFi router to the service provider device. Not all Macs these days come with an Ethernet port. I have a couple of adapters that allow me (if I were to need it) to connect the MacBook Pro to an Ethernet connection. These are more secure and faster. Goodrich writes, that the original Ethernet was inspired by the ALOHA-net packet radio network and the ARPANET. ALOHAnet was a radio based technology that transmitted packets of data, confirming something I tell my students: that new technologies do not appear out of the air; there is usually something that precedes them, from which they borrow.

As a note, I always ask my students the meaning of modem. They are of course able to explain basically what it does, but until they understand the derivation, may not understand the significance: modulate/demodulate. It changes analogue signals to digital and vice versa. The first demonstration I saw of this was in 1985 at the library of the US university I was at. Rubber cups were put over the mouth- and earpiece of a telephone handset and the device these were attached to converted the signals so that one computer could communicate to another, wherever it was in the world.
At the time communications were mostly localized. The significance of this in a world where communication between personal devices was almost unheard of, made me understand the potential of what could be coming. That was emphasised when the iPhone was introduced in 2007. While the mention of the touchscreen iPod and a mobile phone had rapturous applause, the third feature of an "internet communications device" was clearly lost on most of the audience at the Moscone Center. Consider how we use out smartphones now.
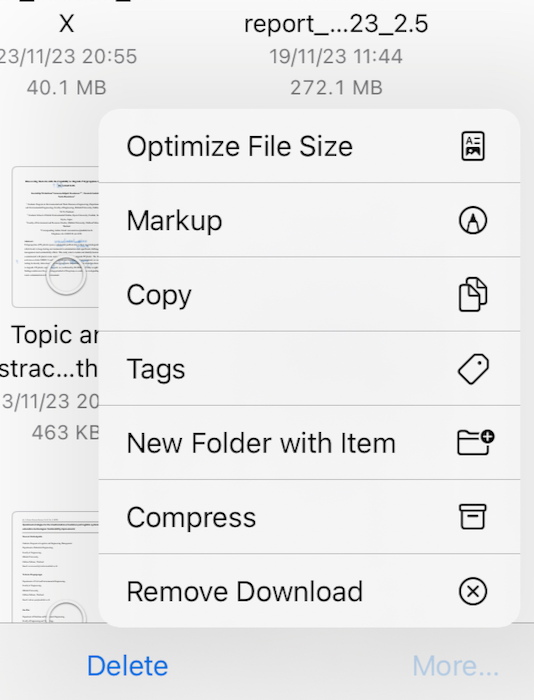 It is always nice to have feedback. A few days ago I wrote about a solution to the bloated PDF files I have been seeing on iPads when I edit them and use markup. In exasperation, after having a 1.6MB file reach over 90MB when I was about halfway through editing it, I took steps to reduce its size. The engorgement was partly a result of the multiple saves needed since iPadOS 17 was released as every few minutes, when using markup, the file would go back to the first page and any markup not saved was lost.
It is always nice to have feedback. A few days ago I wrote about a solution to the bloated PDF files I have been seeing on iPads when I edit them and use markup. In exasperation, after having a 1.6MB file reach over 90MB when I was about halfway through editing it, I took steps to reduce its size. The engorgement was partly a result of the multiple saves needed since iPadOS 17 was released as every few minutes, when using markup, the file would go back to the first page and any markup not saved was lost.
My first intention was to split the file: cut it in half so email would accept the smaller size of the 2 parts. When I did this, the size was reduced to about 10% of the original. I tried another file of around 132MB and that went down to under 10MB. Why could I not do something like this on the iPad? After all many people nowadays work only on handheld devices.
After a couple of attempts I found that with the file unopened (and displayed in the Files window, using Select, highlighting the file then using More at the bottom of the screen revealed a menu. The top item was Optimize File Size and that did the job.
A message from a reader (Mel) commented on this and noted that he too had had problems with file-bloat when using PDF files in Graphic Converter. His solution was to use compression on the website online2pdf.com to reduce the pdf file size. It has an easy-to-use interface and is worth looking at. I have bookmarked this. Redundancy is good.
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. After 3 years writing a column in the Life supplement, he is now no longer associated with the Bangkok Post. He can be followed on Twitter (@extensions_th)
For further information, e-mail to
Back to
eXtensions
Back to
Home Page