|
|
Friday Comment: Apple Silicon Threats; Robocup 2022; Super Pumped and Sideloading; CSAM, CSEA and the UKBy Graham K. Rogers
I have been really happy with my recent Apple purchases: iPhone 13, M1 MacBook Pro, M1 iPad Pro and the iPad mini. I had been anticipating Apple silicon since the iPad with A7 chip when it was clear Apple was able to create advantages that other manufacturers could not hope to follow. The move to 64-bit apps was a masterstroke that gave an advantage of several months; and some security features such as the Secure Enclave were unique. Fingerprint ID and Face ID were well-executed on both handheld devices and Macs (with the T2 chip and then M1). The performance of these new devices is outstanding, and they run cooler too as less energy is used. With the moves to work from home and the arrival of Apple silicon, sales of Macs have accelerated considerably. The M2 and later the M3 (and more) will push this advantage home, but PC makers are not happy. Jonny Evans (AppleMust) commenting on a report from DigiTimes writes that "Apple's competitors are facing dual headwinds of declining demand for their products while interest in what Apple offers grows." Competitors are concerned that with the new Macs they are going to lose further and there is more to come. My heart bleeds.

Charlton's item summarizes the effects of the legislation accurately: companies will have to "share metrics with competitors, ensure that all apps are uninstallable, not preference their own apps and services, allow users to utilize third-party app stores, payment systems, and app sideloading. . . ." There is more in the second main paragraph that outlines the changes, and this will affect all the major companies. And it will affect users a lot too, many of whom will have their fingers burned, for example when they try sideloading. Apple has already provided information about how it sees the effects of sideloading and I mentioned this a few weeks ago with a link to an item from Patently Apple. The title should be enough to stir users: Apple reports that it stopped $1.5 billion in fraudulent transactions in 2021. That article is worth reading again in the light of this pending legislation, particularly the summary of Apple's report on this. The Patently Apple report uses much of the Press release from Apple. Note also (in another report from Patently Apple - and several other online sources) that several security experts, "including two ex-CIA directors and a past NSA director", have provided Apple with support on the question of sideloading and they see the risks, even if the EU and CMA will not. One of those experts is General Michael Hayden who received some notoriety for his comment in a debate: we kill people based on metadata. My students love that; but I put it into context and outline how General Hayden qualified this. Since that revelation he has become a useful sounding board and his pragmatic comments on security are worth considering. If he, John Brennan, Mike McConnell and others see risks from sideloading, then the EU should too: "Requiring Apple devices to accept third-party apps and app stores necessarily increases the risk of malware on iOS devices, which directly correlates to an increased risk to national security. . . ."
The Patently Apple description of the Showtime series, including meetings between Tim Cook, Eddy Cue and Travis Kalanick, so intrigued me that I ordered the book. I am still only halfway through this, but a few days ago read the chapter titled, "The Apple Problem" (153-164). This has some meetings but not all of those described in the article. As Patently Apple writes, "The depths of deceitfulness by Uber was a perfect example of what companies are willing to devise in order to get around Apple's privacy rules and collect data on customers and their competitors." This is why app (and phone) security should not be left to bureaucrats. Note that it was revealed that Facebook staff are able to access deleted user data and share the information with law enforcement (Pesala Bandara, PetaPixel) and they sacked the whistleblower. Note that Facebook tells users, "that once content was deleted . . . it would not remain on any Facebook servers and would be permanently removed." Not so, apparently.
However, as many have argued, these identifying hashes could be substituted for faces of those who are deemed to be enemies of a government; and that government could theoretically insist that Apple identified users with these images on their phones. Like many examples of technology it can be used, or it can be abused. Although it may be put on hold with the current political situation in the UK, the Online Safety Bill keeps having amendments tacked on to it without proper debate and this week a number of sources, including Patently Apple are reporting that "The UK will compel technology companies to find ways to identify and remove child abuse images from their platforms. . . ." It has been suggested that to comply with this, Apple could implement CSAM in the UK, although the original plan was USA first. Katyanna Quach (The Register) points out that the UK Government "wants communications, encrypted or not, to be screened for CSEA material". CSAM is child sex abuse material while CSEA is child sexual exploitation and abuse. The change here is that this legislation wants the authorities to be able to ignore encryption; or at least the companies must be able to do this and report any abuse. As with criticism about Apple's CSAM plans, Quach notes that, "Netizens may also not trust that just CSEA content is being reported."
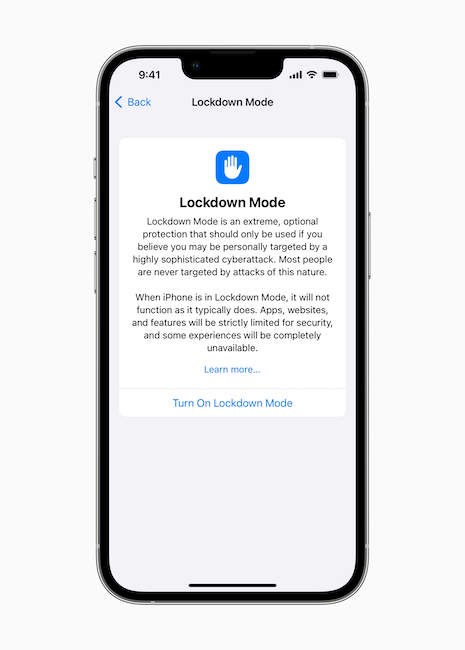
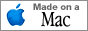
CSAM Technical Information (left) and Apple's new Lockdown Mode - Image courtesy of Apple
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. After 3 years writing a column in the Life supplement, he is now no longer associated with the Bangkok Post. He can be followed on Twitter (@extensions_th) |
|


 A number of sites commented on the EU development, with
A number of sites commented on the EU development, with  Patently Apple has been "on point" with this and related questions. I was intrigued by a link to an article on a Showtime series, Super Pumped - The Battle for Uber: "A story of ambition and deception, obscene wealth, and bad behavior that explores how blistering technological and financial innovation culminated in one of the most catastrophic twelve month periods in American corporate history." I copied that from the back cover of the book.
Patently Apple has been "on point" with this and related questions. I was intrigued by a link to an article on a Showtime series, Super Pumped - The Battle for Uber: "A story of ambition and deception, obscene wealth, and bad behavior that explores how blistering technological and financial innovation culminated in one of the most catastrophic twelve month periods in American corporate history." I copied that from the back cover of the book.