|
|
Sunday Comment: Apple CSAM - Bound to Succeed, Destined to FailBy Graham K. Rogers
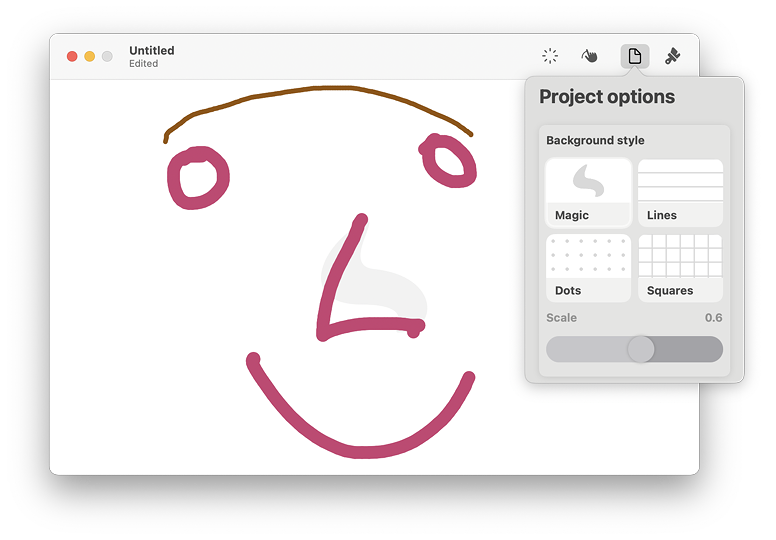
When explaining ideas, I could quickly make a sketch to illustrate the idea. If I know I might need to sketch something, I can attach the iPad and share the screen; but (no matter what bureaucratic experts claim) it is impossible to plan for the unknown in classes and I sometimes need spontaneous input.
The panel is not full screen, but matches the size of the trackpad. It takes some adjustment from the user, but a line drawn on the panel begins where the finger is placed. I had to learn to remove my finger quickly otherwise the line would continue. There are style options and a number of brush options, including several colors. The app is fairly rough and ready, but at a pinch it may allow that connection to be made between my ideas and the students' understanding.
Politicians write the laws and sometimes they are wrong (politicians and laws). In some countries and at some historical moments, legislation is created for vindictive reasons. Some laws are knee jerk reactions to a situation, like the Australian reaction to refugees arriving from Afghanistan in leaky boats some 20 years ago. Most laws, however, are written to deal with what politicians see as a need to control a particular situation, group or problem. One of the concepts that US politicians (and others) react to strongly is that of monopoly. They have had much experience of this for example with Carnegie and J.P. Morgan and the control of steel, while the control of media throughout the world, particularly by the Murdoch Corporation could be improved. More modern influences are often referred to as Big Data although the more well known of these like Amazon, Apple, Facebook, Google (and to a lesser extent Twitter), operate in different ways. Politicians find it easier to group them, while conveniently ignoring the ways in which mass media (newspapers, television) sway public opinion. Google and Apple have their own problems with politicians in Europe, UK, USA and now Australia partly because they are just big. To some that automatically equals a monopoly situation, although there are differences. Facebook has grown into a major influencer, partly helped by the tools that Cambridge Analytica introduced that created an awareness of how social networking could influence voters and buyers. And how this sells advertising. It's growth has been rapid and the CEO, Mark Zuckerberg has appeared in front of US politicians and their committees a number of times. This may not have helped at all as he comes across as bland, emotionless and evasive. Even Tim Cook, who had a reputation as a grey man, is more enthusiastic and at least answers any questions posed (up to a point).
It has changed some more recently (although I am enjoying the Reels) and I am switching to Glass, a new app that is aimed at photographers who just want to display their output. It is a bit slow at the moment and slightly limited, but with all these things, it may benefit from user input and suggestions. Last week Juli Clover (MacRumors) wrote about the antitrust case that the Federal Trade Commission (FTC) has been building against Facebook, and notes that this has now been reinforced with "more detail on how the company either crushed or bought out its rivals in an attempt to get rid of competition". This strengthens its case against the company and it has asked the judge "to force Facebook to sell Instagram and WhatsApp." The details in the article taken from the FTC complaint suggest that while Facebook originally based its approach on the desktop, mobile computing left it wanting and its buy and bury approach helped it overcome this, along with hindering integration 3rd-party developers on its platform.
although Apple may have shot itself in the foot on that last one (see below). Apple has always complied with any legal warrants that have been issued, as do all of the Big Data companies, but if there is end to end encryption, not even Apple (or WhatsApp) can provide the unencrypted data. Last week it was reported (Oliver Haslam, Redmond Pie) that a Bill introduced into the US Senate is aimed at any phone maker, although how that will be applied to phones using Android made in Asia has me scratching my head. An immediate oddity is the Section describing the scope, that begins "A device manufacturer that sold more than 1,000,000 consumer electronic devices in the United States in 2016 or any calendar year thereafter", which immediately offers a get out to those criminals who would depend on encryption. This was used by Anom (although the FBI were secretly running that) and particularly, EncroChat which served criminals for a while until it was broken into. Both of these had a small number of subscribers: well below 100,000 so the phones would not have been included, should this legislation succeed. Apple (and others) do hand over information when a lawful warrant is executed, which users agree to with the licensing. That encryption is the key to privacy.

Current iPhone 12 - image courtesy of Apple
Of course, as Apple and Correllium already have conflicts, one questions the sincerity here. Stephen Warwick (iMore) also comments on the offer, which on the face of it sounds useful: independent verification of continued privacy. He notes that the case between the two was settled just a week ago "over the very iOS virtualization software it says can now aid security researchers." Curious. Apple has now announced an appeal to the court decision in its case.
While some of the criticism of Apple's approach to this has tended to be knee-jerk, for example the comments from Bill Maher (Stephen Warwick, iMore) who adds on other derogatory comments about iPhone owners, because he can: a man who likes the sound of his own opinions. Most criticism, however, is well-intentioned. The idea of Apple reneging on its famed privacy protection is beyond belief to many. There has been a lot of expert input, including from some computer scientists from Princeton who had already developed a CSAM system, Stephen Warwick reports in iMore. They warn against Apple doing the same, writing in The Washington Post that this is not because they do not understand how it works, "The problem is, we understand exactly how it works." As Warwick writes, this protection that Apple claims exists to prevent the use of the system in identifying other types of images, is not technological. It is a policy decision; and policy can be changed. Note, for example, while we are already aware how China controls what internet users in the country can access, and Russia insists that certain apps are installed when the iPhone is delivered to customers in the country, Apple (along with Google) is now being forced to remove an app developed by opposition leader, Alexei Navalny (Stephen Warwick, iMore), because "it is used to promote the activities of organizations recognized as extremist". Navalny who opposes Russian President, Vladimir Putin, was famously poisoned in August 2020.

Several commentators have already expressed an intention to use alternative products, although this cure may be just as bad with the current options available. Having spent years building a reputation based on its regard for privacy - which it still has - in one fell swoop that is to be lost. With CSAM detection Apple is destined to fail. Damned if you do. Damned if you don't.
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. After 3 years writing a column in the Life supplement, he is now no longer associated with the Bangkok Post. He can be followed on Twitter (@extensions_th) |
|


 I was alerted to a Mac app called Magic, by
I was alerted to a Mac app called Magic, by  On the way to creating itself, Facebook has absorbed several companies, some of which may have been erstwhile competitors. Instagram and WhatsApp are two of the most well-known. With both, users have been disappointed with the way changes have been introduced. With Instagram this has been most upsetting for photographers who had been using the app to build recognition.
On the way to creating itself, Facebook has absorbed several companies, some of which may have been erstwhile competitors. Instagram and WhatsApp are two of the most well-known. With both, users have been disappointed with the way changes have been introduced. With Instagram this has been most upsetting for photographers who had been using the app to build recognition.