Cassandra: Headphone Security - Different Approaches Taken by iOS and Android

AMITIAE - Thursday 23 June 2016
|
Cassandra: Headphone Security - Different Approaches Taken by iOS and Android |
 |
|
|
By Graham K. Rogers
Not that I want to debate the merits of these output methods, but I hope that the Lightning port option is what Apple decides on, from the points of quality, a reduction in internal components (hence more space for battery) and the point that the technology is rather long in the tooth. I am well aware that others will disagree with these points. So be it.

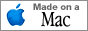
An investigation found that such a faulty cable caused erroneous input. Such variations could be used to hijack an Android device. The two systems handle input through the standard headphone jack in different ways.
Gould reports that iOS devices only react to a single change in voltage: when the button on the headphones is pressed. This button is situated in the cable to the right earbud. Again, were the cable frayed, this could cause either an interruption to the sound output, or turn the delivery on and off intermittently.

Control button in right earbud cable
Full details of his tests and the extended potential for security risks are in his paper, AudioJacked - Theft of Money and Information Through a Phone's Audio Port.
Graham K. Rogers teaches at the Faculty of Engineering, Mahidol University in Thailand. He wrote in the Bangkok Post, Database supplement on IT subjects. For the last seven years of Database he wrote a column on Apple and Macs. He is now continuing that in the Bangkok Post supplement, Life. |
|
For further information, e-mail to
Back to
eXtensions
Back to
Home Page